A new vulnerability was found in the open source library “OpenSSL”.
It is called the heartbleed bug. This bug allows an attacker to get the private keys for an HTTPS Server that is running OpenSSL.
This bug has affected some of the biggest sites out on the Internet. From Amazon to Netflix.
Enterprise Remote Control uses OpenSSL for its web interface, and if you are running it – you need to patch it immediately.
What is possible with this bug? If an attacker is on the same network, or can somehow get between you and your server (Man in the middle) he would be able to decrypt the traffic. In most situations this would be difficult – but it is not impossible. Especially if you are accessing the enterprise server from a coffee shop or other public network access.
Lets get down to business. There are two ways to patch.
The first way is to install the new build we have with the fix. It will take possibly 30 minutes of downtime.
Here is the download link:
Just run the setup package, and it will automatically upgrade your server for you.
The second way takes less time, but requires a little more work:
-Stop the IntelliAdminERC service (At the command line type net stop intelliadminerc)
-Copy and overwrite these two files to C:\Program Files (x86)\IntelliAdmin\Enterprise\Reflector\WebServer
-Start the IntelliAdminERC service (At the command line type net start intelliadminerc)
For either fix – you will want to re-generate your certificate just in case someone has gotten your private key. If you did not setup your own certificate you can regenerate by going into the enterprise server settings and pressing the “Use Self Signed” button:
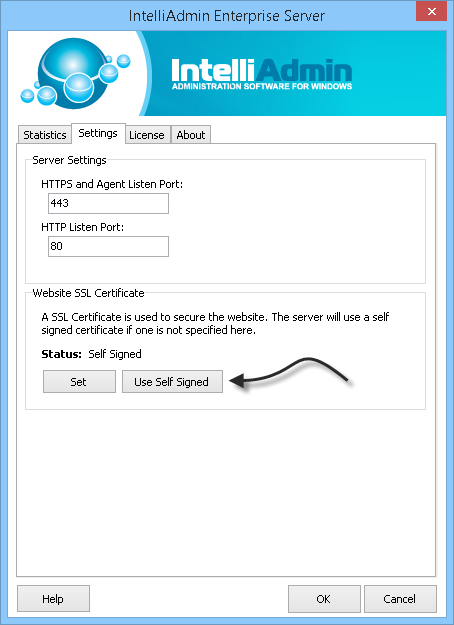
This will force the server to generate a new self signed cert.
If you purchased a cert, then you will need to get it re-issued. Because of how widespread this issue is – your certificate provider should have a process in place for this soon, if not already.
If you have any questions, please feel free to email us at support@intelliadmin.com
One more thing…Subscribe to my newsletter and get 11 free network administrator tools, plus a 30 page user guide so you can get the most out of them. Click Here to get your free tools

{ 4 comments… read them below or add one }
Hi Steve,
We really appreciate the speed at which you have updated the enterprise server. We have other vendors who don’t even have an eta when it will be fixed. You guys have a fix out almost the moment I found out about this problem!
Thanks for the quick update steve.
We followed the update and yes it replaced/fixed the two dll’s.
However, what is being done about the openssl.exe in the openssl folder:
C:\Program Files (x86)\IntelliAdmin\Enterprise\Reflector\OpenSSL
running “openssl.exe version” in that folder shows its vulnerable: “OpenSSL 1.0.1e 11 Feb 2013”
Hi Jason,
That is only used to generate certificates…and is only run during the install to create a self signed cert.
You are welcome to update that as well, but it is not a security flaw for the configuration of our software.
Thanks,
Steve