This tip is only for Vista….so I apologize in advance to those of you still using XP. In Vista you can easily clear your browsing history by going into the options of Internet Explorer. I have helped a few organizations that use this information after a spyware incident to determine where the problem came from.
Users may notice that something happened, and call the IT department for help. Before they do that they clear their history so they don’t get in trouble. This vital information is now lost, and a potentially bad site could cause the problem again.
So how could you prevent this? Easy, use group policy. You can do this locally, or on your domain controller if you want to apply the changes across your network.
To change the policy on your Vista machine, click on the start button, and type gpedit.msc – then press enter.
Then the local policy window will be displayed. You will need to drill down to:
Computer Configuration->Administrative Templates->Windows Components->Internet Explorer\
Once you are in that section, scroll down and you will see three items:
“Turn off ‘Delete Browsing History’ functionality”
“Turn off ‘Delete Passwords’ functionality”
“Turn off ‘Delete forms’ functionality”
Only the first one is necessary for what we are trying to accomplish, but the other two are related and you may want to use them.�
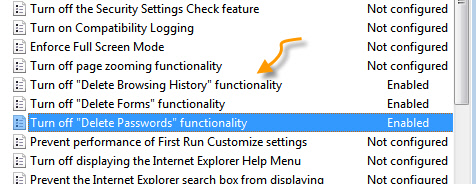
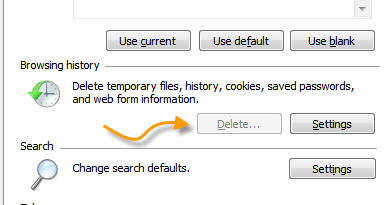
I am not a big fan of how many policy items are worded. It forces you to enable them when you want something disabled. So if you want to disable them, then use the enable option. Now, if you go into internet explorer, and try to clear the history, you will notice that the button is disabled:
This same tip could be used on a domain controller. If you have 2008 it will already be available. On some versions of 2003, you will need to get the updated administrative template for Internet Explorer.
One more thing…Subscribe to my newsletter and get 11 free network administrator tools, plus a 30 page user guide so you can get the most out of them. Click Here to get your free tools

{ 7 comments… read them below or add one }
I really don’t care if my end-users delete their history or not. For ones, it is against my IT policy in even using IE in the first place. Firefox is the only approved web browser.
Two, the firewall prevents all traffic leaving the corporate office without going through a proxy server. Therefore, every website is logged as is their user name, date, time, web browser used, … Therefore I can see the logs, error codes from IIS, Apache, etc. rather than drilling into their cache, history, etc., especially if they use Firefox, Opera, Safari, Konquerer, no matter what OS, browser, etc.
And I really don’t see how viewing their web history will help diagnose any spyware problem. I personally would first use, after a run of all relevant anti-spyware tools (e.g., Spybot S&D, AdAware, and Windows Defender), a full scan with Symantec Endpoint Protection, then if problems persist, use Hijack this and figure out what is causing it.
Though I do agree with you on the wording of policies, I always have to read and reread multiple times to make sure I am doing what I intend. I would guess Microsoft did that intentionally, just to forceus to pause for a moment to make sure we don’t fubar things up!
I contend that it *is* relevant. There have been many cases where a machine has been infected with spyware…I can see the timestamps of the spyware ActiveX files and I can directly connect this to a website visited. Sure you could clean the system, but if you can’t directly prove where that user visited and how it connected to the infection, it may be hard enforcing more restrictive web browsing on that user.
Perfect example. 5 years ago I was working at an insurance company, and the Vice President of sales had been visiting a gambling site over and over. Each time this would install spyware on his system. I tried getting his access blocked (To that site), but I was stopped at every turn. The next time I took the history, matched it up with the time stamps on the Dlls for the spyware and I proved my case.
Second example. Not really an example, but in many corporations you have black-lists for websites. If your firewall, and your content filter still miss the bad site, you can use this forensic information to directly link an infection to a website, and thus ban the site.
So the usage is two fold, you can use it to zap users (not something I really like), and second so you can ban the site outright from your organization…since we all know content filters, and firewalls can’t do it all.
They disabled this at my school. But you can still delete the browsing history. Just right click where the tabs are, enable Menu Bar, click tools, then Click on Delete Browsing History, and viola, history and cache deleted. Dont know if you can fix that, but just something you might want to know.
I also block all ActiveX so rogue scripts wouldn’t come in. My manager and I are both very paranoid what goes into our network (we block all non corporate webmail, streaming audio/video), zip, com, exe, bat, scr., … are all blocked from being downloaded. While it is mostly blacklisted sites (discussion forums from users that don’t like working but like going to their War of Warcraft sites instead), we are very selective of which MIME types can be downloaded from a web browser. While this method does make internet based activation VERY annoying, it does a very good job in preventing people from screwing things up.
Since my company does transfer HUGE amounts of data, we do allow USB/IEEE 1394 HDD/jump drives/etc, and there is a risk in getting viruses spread that way, but all users are Power Users and are unable to install anything to begin with. Our group policies are restrictive enough to prevent 90% of problems, but still allows people to do their jobs.
This is also available in XP. As are forms and paswords.
Group Policy -> User -> Administrative Templates -> Windows Components -> Internet Explorer
Same wording (enable to disable). Same flaw (as in, it is still on the tools menu).
I am trying to stop deletion of history and temp internet files. I used group policy to prevent them from doing this from IE7. That’s great, BUT if the user is not computer illiterate he can simply navigate to his History file and delete manually. I have tried tweaking the file permissions for hours and can’t seem to prevent this.
Good point. This may be difficult to prevent, since by nature IE needs to have read/write access to this file. One way would be to do advanced permissions…and allow everything but delete access. They could still open it with an editor and truncate it…but that would take another level of knowledge to accomplish. I think once a user is this sophisticated, the standard tools are not going to stop anything.